Key Points
Your attack surface is made up of all the digital assets that can be used to gain access to your network or sensitive data. Anything on-premise, in the cloud, in subsidiary networks, and in third-party environments. Anything that a hacker can attack.
Today, keeping track of all these IT assets can be challenging. On top of all your remote devices, you may also need to monitor IoT sensors and SaaS accounts, as well as your web applications, virtual machines, containers, and more - that’s where asset discovery tools come in.
What is asset discovery?
Asset discovery is the first step in managing this attack surface. It shows you what assets you have, and what could be exposed. This is essential for keeping an up-to-date inventory, because if you don’t know what you have, how can you protect it?
As companies grow, different teams, departments and contractors start spinning up new infrastructure. Even if you have good internal tracking of assets, performing external attack surface discovery can help you find some of this shadow IT that your processes might miss.
Asset discovery is therefore a key element of attack surface management that helps you to manage and monitor all your hardware and software. You can see what assets you have, where they are, who’s logged on, what’s exposed, and what need patching or updating.
Traditionally, asset discovery was a times-consuming and labor-intensive task – modern automation tools can do some of the heavy lifting, such as keeping software licences up-to-date and compliant – unpatched vulnerabilities are responsible for up to 60% of all data breaches.
But make no mistake, there’s still a fair amount of manual work involved in asset discovery. These asset discovery tools help you pull in more data sources faster, but you still need to interpret the results and feed the data between the tools.
Best asset discovery tools
BGP Toolkit
Hurricane Electric’s BGP Toolkit allows you to search companies to find their autonomous system numbers (ASNs), and then look up IP ranges associated with those ASNs.
Key benefits
- Gives insight into internet routing with ease in a user-friendly way.
crt.sh
Certificate transparency means there’s a log of every SSL certificate available to the public, including domain names; crt.sh is a great tool to find this info and new domains.
Key benefits
- Present certificate transparency information in an easily searchable format
- API endpoint allows easy integration with scripts and other tools
- Helps detect maliciously or accidentally mis-issued certificates that may be abused to impersonate them and rogue CAs can be identified more easily and reliably
Intruder
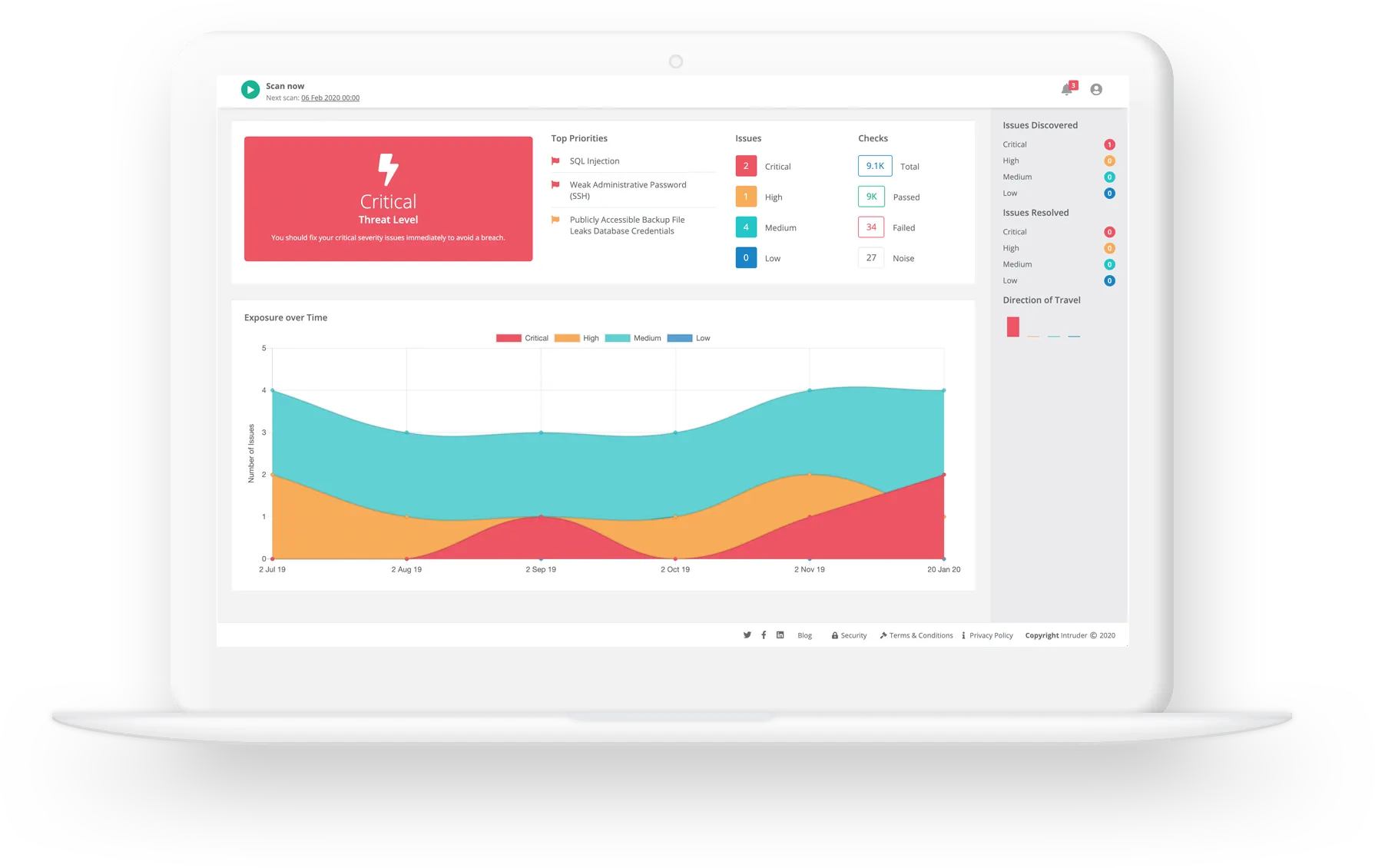
Intruder’s automated vulnerability scanner can help you identify and monitor your internal and external assets for auditing, logging, threat modelling and reporting, so you can assess your security issues and risk at any given time.
Key benefits
- Shows where and how your company may be vulnerable
- Filters noise so you can fix issues that matter most
- Proactive emerging threat scans minimize exposure
CertStream
CertStream is an intelligence feed that gives real-time updates from the Certificate Transparency Log network to use as a building block to make tools that monitor new SSL certificates being issued in real time.
Key benefits
- Allows quick oversight and reaction to domains found in newly issued certificates
- Does the hard work of watching, aggregating, and parsing the transparency logs
- Gives simple libraries that enable you to target domains with minimal effort
Katana
Katana is designed to crawl websites to gather information and endpoints – including headless browsing. This means it can crawl single-page applications (SPAs) built using JavaScript, Angular, or React. These types of applications are becoming increasingly common but can be difficult to crawl using traditional tools.
Key benefits:
- Can crawl for multiple domains and subdomains simultaneously
- Easily customizable in scope, rate limiting, filters, outputs, and modes
Shodan
Internet database scanners are another way to discover new assets. Tools like Shodan are designed to map and gather information about internet-connected devices and systems, help you find out who is using various products, and how they're changing over time.
Key benefits
- Detects devices that are connected to the internet at any given time, the locations of those devices and their current users
- Includes networks, surveillance cameras and industrial control systems (ICS)
- Provides filters to improve search efficiently
Censys
Censys offers external asset discovery and exposure management with a real-time, contextualized view into all of your exposures across the internet and cloud. Like Shodan, it scans the entire IPv4 range of the internet to find exposed services and presents them in a searchable format.
Key benefits
- Multiple cloud connectors including Azure and AWS
- Manual and automated addition of IP and domains/subdomains
- Reporting and risk dashboard with ability to modify risk severity
Security Trails
Public datasets like SecurityTrails collect data from multiple sources, some of which may not otherwise be available to you. These can be used to discover more domains and subdomains belonging to an organization without active enumeration.
Key benefits
- Provides a huge dataset and collects from sources you otherwise wouldn’t be able to
- Manages infrastructure sprawl and finds forgotten digital assets
- Their API allows good integration and is easy to work with
DNSDumpster
Online passive scanning tools like DNSdumpster can be used to obtain information about domains, block addresses, emails, and all information DNS related. Understanding network footprinting and reconnaissance methodology can help inform an organization’s security posture.
Key benefits
- As a web- based service, you only need to navigate to their URL and query your target
- Provides results in a downloadable format for passing into other tools
- Presents a relational picture that binds all records
sublist3r
Subdomain brute forcing is the process of saying “does this subdomain exist” over and over again at speed. Many tools do this, such as sublist3r which is designed to enumerate subdomains using brute forcing, as well as OSINT (open-source intelligence) to help penetration testers and bug hunters.
Key benefits
- Fast subdomain brute forcing can yield results that wouldn’t be found by other sources
- Enumerates subdomains using search engines such as Google, Yahoo, Bing, Baidu and Ask and subdomains using Netcraft, Virustotal, ThreatCrowd, DNSdumpster and ReverseDNS
AssetNote Wordlists
When performing subdomain brute forcing, you need a good wordlist to help discover the best subdomains. AssetNote's "best DNS" wordlist has 10 million lines in it, and in their words, “you'll find that you discover some pretty obscure subdomains using this wordlist”.
Key benefits
- Find subdomains that are less well-protected than the root domain or the target
Why you should add Intruder to your asset discovery armory
While not a specialist asset discovery tool, Intruder gives a real-time view of your attack surface through continuous network monitoring, automated vulnerability scanning, and emerging threat scans in a single platform.
With downloadable reports to aid compliance and actionable remediation advice, Intruder helps nearly 3,000 customers around the world to focus on fixing what matters, making vulnerability management easy and effective.
Intruder automatically connects your cloud accounts, notifying you of any changes to your cloud assets, providing insights and advice to help protect your attack surface. Why not try Intruder for free for 14 days and see how we can help protect your attack surface?